Postgres.app is a full-featured PostgreSQL installation packaged as a standard Mac app.It includes everything you need to get started:we've even included popular extensions like PostGIS for geo data and plv8 for JavaScript.
- Postico 1 3 3 – A Modern Postgresql Client Permissions Download
- Postico 1 3 3 – A Modern Postgresql Client Permissions Failed
- Postico 1 3 3 – A Modern Postgresql Client Permissions Server
- Postico 1 3 3 – A Modern Postgresql Client Permissions Command
Postgres.app has a beautiful user interface and a convenient menu bar item.You never need to touch the command line to use it – but of course we do include all the necessary command line tools and header files for advanced users.
If that doesn't suit you, our users have ranked 35 alternatives to Postico and many of them are available for Windows so hopefully you can find a suitable replacement. Other interesting Windows alternatives to Postico are HeidiSQL (Free, Open Source), DataGrip (Paid), pgAdmin (Free, Open Source) and Valentina Studio (Freemium). Berkeley Electronic Press Selected Works. If this is not acceptable in your environment, follow the steps for version 9.1 above to use a dedicated service account. For all PostgreSQL versions on a domain: 'postgres' as a domain account. After the installation, PostgreSQL 9.1 or below is running under a local account named 'postgres'. 9.2 or above instead install into NETWORKSERVICE. The PostgreSQL Global Development Group remains committed to making PostgreSQL available as free and open source software in perpetuity. There are no plans to change the PostgreSQL License or release PostgreSQL under a different license.
Postgres.app can install minor updates automatically, so you get bugfixes as soon as possible.
Installing Postgres.app
Download ➜ Move to Applications folder ➜ Double Click
If you don't move Postgres.app to the Applications folder, you will see a warning about an unidentified developer and won't be able to open it.
Click 'Initialize' to create a new server
Configure your $PATH to use the included command line tools (optional):
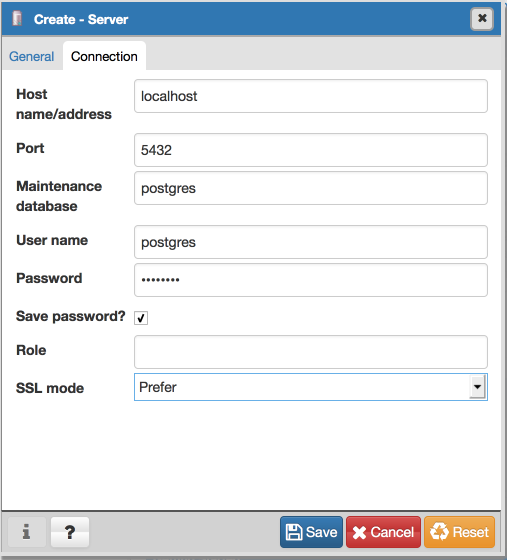
Done! You now have a PostgreSQL server running on your Mac with these default settings:
| Host | localhost |
| Port | 5432 |
| User | your system user name |
| Database | same as user |
| Password | none |
| Connection URL | postgresql://localhost |
To connect with psql, double click a database. To connect directly from the command line, type psql. If you'd rather use a graphical client, see below.
NOTE: These instructions assume that you've never installed PostgreSQL on your Mac before.If you have previously installed PostgreSQL using homebrew, MacPorts, the EnterpriseDB installer, consider removing other PostgreSQL installations first.We also have instructions for upgrading from older versions of Postgres.app.
Graphical Clients
Postgres.app includes psql, a versatile command line client for PostgreSQL.But it's not the only option; there are plenty of great graphical clients available for PostgreSQL.Two popular tools are:
pgAdmin 4 is a feature rich open source PostgreSQL client.It has support for almost every feature in PostgreSQL.The only downside is that the cross-plattform UI really doesn't live up to the expectations of a native Mac app.
Postico on the other hand, is a very modern Mac app.It's made by the same people that maintain Postgres.app, and we think you'll like it! We put a lot of effort into making it a joy to use.However, it doesn't have the extensive feature set of pgAdmin, and it's a commercial app rather than open source.
Postico 1 3 3 – A Modern Postgresql Client Permissions Download
Aside from those two options, there are a lot more to choose from! Check the documentation for a list of amazing Mac apps for PostgreSQL.
How to connect
After your PostgreSQL server is up and running, you'll probably want to connect to it from your application.Here's how to connect to PostgreSQL from popular programming languages and frameworks:
To connect from PHP, make sure that it supports PostgreSQL. The version included with macOS doesn't support PostgreSQL. We recommend MAMP for an easy way to install a current version of PHP that works.
You can use PDO (object oriented):
Or the pg_connect() functions (procedural):
To connect to a PostgreSQL server with Python, please first install the psycopg2 library:
Django
In your settings.py, add an entry to your DATABASES setting:
Flask
When using the Flask-SQLAlchemy extension you can add to your application code:
SQLAlchemy
To install the pg gem, make sure you have set up your $PATH correctly (see Command-Line Tools), then execute the following command:
Rails
In config/database.yml, use the following settings:
Sinatra
In config.ru or your application code:
ActiveRecord
Install the activerecord gem and require 'active_record', and establish a database connection:
DataMapper
Install and require the datamapper and do_postgres gems, and create a database connection:
Sequel
Install and require the sequel gem, and create a database connection:
- Download and install the PostgreSQL JDBC driver
- Connect to the JDBC URL jdbc:postgresql://localhost
For more information see the official PostgreSQL JDBC documentation.
libpq is the native C client library for connecting to PostgreSQL. It's really easy to use:
Now compile the file with clang and run it:
You can just use the C API in Swift! First include libpq in your bridging header:
Then make sure to link with libpq.
On iOS, you'll need to build libpq yourself.
On macOS you can use the system provided libpq (does not support SSL) or use libpq provided by Postgres.app by adding the following build settings:
| Other Linker Flags | -lpq |
|---|---|
| Header Search Paths | /Applications/Postgres.app/Contents/Versions/latest/include |
| Library Search Paths | /Applications/Postgres.app/Contents/Versions/latest/lib |
Now you can use the libpq C library to connect to PostgreSQL:
Support
We have a list of common problems in the troubleshooting section in the documentation.
For general questions concerning PostgreSQL, have a look at the official PostgreSQL documentation.
If you have a question concerning Postgres.app that is not answered by the Postgres.app documentation,you can ask @PostgresApp on Twitter, or open an issue on GitHub.
When reporting bugs, let us know which version of Postgres.app & macOS you are using, and be sure to include detailed error messages, even if your issue seems similar to another one.
License
Postgres.app, PostgreSQL, and its extensions are released under the PostgreSQL License. The released binaries also include OpenSSL (OpenSSL License), PostGIS (GPLv2), and plv8 (3 clause BSD).
Postgres.app is maintained by Jakob Egger. It was originally created by Mattt Thompson.
Extensions
- acl1.0.2
- Access Control List (ACL) Extension
README
Contents
- Quick Start
- ACE structure
Why do I need this?
You need this extension if you want to restrict access to rows in tables basedon an authenticated user. Access Control List (ACL) has become the de-factostandard for implementing a security model in modern applications. Complexscenarios can be handled by using ACLs without having a complex permissionmodel at the application level.
This document is not intended to be a tutorial on ACLs and security anddescribes the Access Control List Extension only. You can find more informationon ACLs on the sites below.
The extension provides you with a number of special types representing ACLentries (ACEs) and a set of functions that check a user against an ACL.
But wait! There is already the aclitem type. What is wrong with it?
The aclitem is an internal type. Its behaviour may change in a futurerelease without notice, so do not rely on it unless you like livingdangerously. Besides, in a typical mid-tier/server environment, applicationsrarely have separate database accounts for each user, which means that theaclitem type will do little to help you secure your application.
How do I set it up?
If you are running Linux, the easiest way to install the extension is to to usethe PGXN client.
Or if you prefer to stick with the good old Make, you can set up the extensionlike this:
If you are running Windows, you need to run the MSBuildcommand in the Visual Studio command prompt.
The platforms available are x64 and x86 and the configuration are 9.1, 9.2,9.3, 9.4, and 9.5.
Or you can download the latest released zip here.
Then you must copy the DLL from the project into the PostgreSQL's libdirectory and the .sql and .control files into the directoryshareextension.
Once the extension is installed, you can add it to a database.
How can I create an ACL?
Since an ACL is a simple one-dimensional PostgreSQL array, the easiest way tocreate it is from a literal constant.
SQLSELECT '{a/i/postgres=rwd, d//user=r, a//=r}'::ace[];
ACL can have zero or more access control entries (ACE). Every ACE has thefollowing textual representation.
There are two types of ACEs: allow and deny (a and d in a textualrepresentation). The type part is mandatory.
The who part defines for which role this ACE is in effect. There is aspecial identifier ' (empty string) representing everyone.
Mask is a string value that specifies the permissions that are allowed ordenied in an ACE.
For more information on ACLs see ACL Structure section below.
How can I compute an ACL based on a parent ACL?
ACLs are often applied to hierarchical structures. In order to compute a newACL based on a parent ACL, use the following function.
acl_merge(ace[] parent_acl, ace[] acl, bool container, bool deny_first)
The container parameter determines if the ACL is computing for a containerobject or a leaf object.
The deny_first parameter defines if the deny ACEs must be placed first (thisis a default behaviour for all Microsoft products).
For more information on ACL flags see ACL Structure section below.
How can I check if the user has the permission to access the data?
Once you created an ACL, you may want to determine if it grants a current orany particular user a specified set of permissions. In order to do this, useone of the following functions.
acl_check_access(ace[] acl, text mask, bool implicit_allow)acl_check_access(ace[] acl, int4 mask, bool implicit_allow)acl_check_access(ace[] acl, text mask, oid role, bool implicit_allow)acl_check_access(ace[] acl, int4 mask, oid role, bool implicit_allow)acl_check_access(ace[] acl, text mask, name role, bool implicit_allow)acl_check_access(ace[] acl, int4 mask, name role, bool implicit_allow)
The first two check the PostgreSQL current user against the specified ACL whilethe four others take the role to check in its third parameters.
There are two types of acl_check_ functions which take text or int4 asthe mask. Production environments should always use the latter form as itis much more efficient.
The functions return the granted permissions (either as a text or int4,depending on the type of their mask parameters). If no permissions are granted,an empty string is returned.
There is also an additional parameter implicit_allow which controls whetherpermission is granted if it was not explicitly granted or denied in the ACL.
I need custom permissions. Is it possible?
There are 16 custom flags and 16 custom permission (see ACE Structure sectionbelow). How you use them is up to you. Commander 3 1 – advanced two pane file manager word. All the extension functions ignorecustom flags.
Does this work with PostgreSQL 9.5 row-level security?
Yes! The Access Control List Extension integrates flawlessly with PostgreSQLrow-level security. All you need is to add an ACL column to your data tableand define security policies.
```SQLCREATE TABLE file_system (id int PRIMARY KEY NOT NULL, parent_id int, is_directory bool NOT NULL, name text, acl ace[]);
ALTER TABLE file_system ADD CONSTRAINT file_system_parent_fk FOREIGN KEY (parent_id) REFERENCES file_system(id);
GRANT SELECT, INSERT, UPDATE, DELETE ON file_system TO PUBLIC;
ALTER TABLE file_system ENABLE ROW LEVEL SECURITY;
CREATE POLICY file_system_read_policy ON file_system FOR SELECT TO PUBLICUSING (acl_check_access(acl, 'r', false) = 'r');
CREATE POLICY file_system_update_policy ON file_system FOR UPDATE TO PUBLICUSING (acl_check_access(acl, 'w', false) = 'w');
CREATE POLICY file_system_delete_policy ON file_system FOR DELETE TO PUBLICUSING (acl_check_access(acl, 'd', false) = 'd');
CREATE POLICY file_system_insert_policy ON file_system FOR INSERT TO PUBLICWITH CHECK (acl_check_access((SELECT p.acl FROM file_system p WHERE p.id = file_system.parent_id), 'w', false) = 'w');
CREATE FUNCTION file_system_modify()RETURNS TRIGGER AS $$DECLARE v_parent_acl ace[];BEGIN v_parent_acl = (SELECT p.acl FROM file_system p WHERE p.id = NEW.parent_id); IF NOT FOUND THEN IF NEW.parent_id IS NULL THEN -- Only a superuser can add a root directory IF current_user <> 'postgres' THEN RAISE EXCEPTION 'Access denied'; END IF;
END IF;
IF v_parent_acl IS NULL THEN NEW.acl = NULL; ELSIF NEW.acl IS NULL THEN NEW.acl = v_parent_acl; ELSE NEW.acl = acl_merge(v_parent_acl, NEW.acl, NEW.is_directory, true); END IF;
RETURN NEW;END;$$ LANGUAGE plpgsql;
CREATE TRIGGER file_system_insert. BEFORE INSERT OR UPDATE ON file_system FOR EACH ROW EXECUTE PROCEDURE file_system_modify();
INSERT INTO file_system(id, parent_id, name, is_directory, acl)VALUES (1, NULL, '/', TRUE, '{a/c/=r}'), (2, 1, '/home', TRUE, '{a//=rdw}'), (3, 1, '/bin', TRUE, '{a//postgres=rdw,d//=rdw}');
SELECT * FROM file_system;```
id | parent_id | is_directory | name | acl----+-----------+--------------+-------+----------------------------------- 1 | | t | / | {a/c/=r} 2 | 1 | t | /home | {a//=dwr,a/hc/=r} 3 | 1 | t | /bin | {d//=dwr,a//postgres=dwr,a/hc/=r}
Then connect as another user and check how it works.
```SQLSET ROLE test;
SELECT * FROM file_system;```
id | parent_id | is_directory | name | acl----+-----------+--------------+-------+------------------- 1 | | t | / | {a/c/=r} 2 | 1 | t | /home | {a//=dwr,a/hc/=r}
SQLINSERT INTO file_system (id, parent_id, name, is_directory, acl)VALUES(10, 1, '/test', TRUE, '{a//=rdw}');
```SQLINSERT INTO file_system (id, parent_id, name, is_directory, acl)VALUES(10, 2, '/home/test', TRUE, '{a//=rdw}');
SELECT * FROM file_system;```
id | parent_id | is_directory | name | acl----+-----------+--------------+------------+------------------- 1 | | t | / | {a/c/=r} 2 | 1 | t | /home | {a//=dwr,a/hc/=r} 10 | 2 | t | /home/test | {a//=dwr,a/hc/=r}
SQLDELETE FROM file_system WHERE id = 1;
```SQLDELETE FROM file_system WHERE id = 10;
SELECT * FROM file_system;```
id | parent_id | is_directory | name | acl----+-----------+--------------+-------+------------------- 1 | | t | / | {a/c/=r} 2 | 1 | t | /home | {a//=dwr,a/hc/=r}
What if my application does not rely on the PostgreSQL roles system?
You can still use the Access Control List Extension even if your applicationdoes not rely on the PostgreSQL roles system. There are three additional ACEtypes supported.
ace_int4(e.g.a/h/1985=rdw,d//-2015=s)ace_int8(e.g.a/h/0=w,d/oic/1234567890=AB)ace_uuid(e.g.a//00001101-0000-1000-8000-00805F9B34FB=r)
And a set of acl_check_ functions that are slightly different from the onesyou have seen so far.
acl_check_access(ace_int4 acl, text mask, int4[] roles, bool implicit_allow)acl_check_access(ace_int4 acl, int4 mask, int4[] roles, bool implicit_allow)acl_check_access(ace_int8 acl, text mask, int8[] roles, bool implicit_allow)acl_check_access(ace_int8 acl, int4 mask, int8[] roles, bool implicit_allow)acl_check_access(ace_uuid acl, text mask, uuid[] roles, bool implicit_allow)acl_check_access(ace_uuid acl, int4 mask, uuid[] roles, bool implicit_allow)
The third parameter of these functions is an array of roles that yourapplication considers the user has.
How does it impact performance?
It introduces some overhead in the data reading, depending on the type andsize of the ACLs (see Performance Benchmarks below), averaging 25%. It is wayfaster than any existing mid-tier security solution could offer.
I no longer see role names in ACEs! What happened?
Sometimes you will see a number sign (#) followed by a number instead of a rolename.
Or an entry with a special 'x' (INVALID) flag.
It happens when the OID specified in the ACL entry cannot be resolved to a rolename. One of the most likely causes is that the role was deleted. Since ACLsare usually set on a large number of objects, it would be unwise to try toremove invalid entries every time a role is being removed from the system, sothese invalid ACEs remain there until you remove them manually. Anotherimporant reason that makes us provide a reasonable textual representation ofevery ACE is that PostgreSQL uses them to make backups and restores.
Are there any tutorials on how to use the extension and ACLs in an application?
Unfortunately, no, but feel free to write one :)
To build it, just do this:
If you encounter an error such as:
Postico 1 3 3 – A Modern Postgresql Client Permissions Failed
You need to use GNU make, which may well be installed on your system as gmake:
If you encounter an error such as:
Be sure that you have pg_config installed and in your path. If you used apackage management system such as RPM to install PostgreSQL, be sure that the-devel package is also installed. If necessary tell the build process where tofind it:
If you encounter an error such as:
You need to run the test suite using a super user, such as the default'postgres' super user:
Once the extension is installed, you can add it to a database. Connect to adatabase as a super user and do this:
ACE textual representation
Postico 1 3 3 – A Modern Postgresql Client Permissions Server
Examples
a/ihpc/acl_test1=wdd/ox/acl_test1=sa//'acl test2'=dw0a//'test'blah'=AB1d//=
ACE types
Type | Description ----- | ------------------------------------------- ALLOW | Explicitly grants the access to the object. DENY | Explicitly denies the access to the object.
ACE flags
Flag | Mask | Description -------------------- | -------------- | ------------------------------------------------------------------------ INHERIT_ONLY | 0x80000000 (i) | Indicates that this ACE does not apply to the current object. OBJECT_INHERIT | 0x40000000 (o) | Indicates that child objects will inherit this ACE. CONTAINER_INHERIT | 0x20000000 (c) | Indicates that child containers will inherit this ACE. NO_PROPAGATE_INHERIT | 0x10000000 (p) | Indicates that child containers will not propagate this ACE any further. INHERITED | 0x08000000 (h) | Indicates that this ACE was inherited from another container. INVALID | 0x04000000 (x) | Indicates that this ACE must not used while checking permissions. | | Flags from 0x02000000 to 0x00010000 are reserved for the future use. | 0x00008000 (F) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00004000 (E) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00002000 (D) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00001000 (C) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000800 (B) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000400 (A) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000200 (9) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000100 (8) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000080 (7) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000040 (6) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000020 (5) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000010 (4) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000008 (3) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000004 (2) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000002 (1) | Flags from 0x00008000 to 0x00000001 are application-specific. | 0x00000001 (0) | Flags from 0x00008000 to 0x00000001 are application-specific.
ACE permissions
Permission | Mask | Description ---------- | -------------- | -------------------------------------------------------------------------- READ | 0x80000000 (r) | Permission to read the object. WRITE | 0x40000000 (w) | Permission to write the object. DELETE | 0x20000000 (d) | Permission to delete the object. READ_ACL | 0x10000000 (c) | Permission to read the ACL of the object. WRITE_ACL | 0x08000000 (s) | Permission to modify the ACL of the object. | | Permissions from 0x04000000 to 0x00010000 are reserved for the future use. | 0x00008000 (F) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00004000 (E) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00002000 (D) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00001000 (C) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000800 (B) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000400 (A) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000200 (9) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000100 (8) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000080 (7) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000040 (6) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000020 (5) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000010 (4) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000008 (3) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000004 (2) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000002 (1) | Permissions from 0x00008000 to 0x00000001 are application-specific. | 0x00000001 (0) | Permissions from 0x00008000 to 0x00000001 are application-specific.
ACE who
There is a special identifier ' (empty string) representing everyone.
Postico 1 3 3 – A Modern Postgresql Client Permissions Command
Intel(R) Core(TM) i5-3470 CPU @ 3.20GHz (fam: 06, model: 3a, stepping: 09)
Linux 3.13.0-generic Ubuntu SMP x86_64, PostgreSQL 9.4.4
~ 20 entries in each ACL
ACE type | Checks per sec | Read rate, records per sec | Read overhead -------- | -------------- | -------------------------- | ------------- OID | 3.2 million | 0.48 million | 18% int4 | 2.4 million | 0.55 million | 29% int8 | 2.9 million | 0.48 million | 20% UUID | 1.6 million | 0.42 million | 36%
Access Control List Extension is distributed under the terms of BSD 2-clauselicense. See LICENSE or http://www.opensource.org/licenses/bsd-license.php formore details.
